In legal AI, the real risk isn’t just what a model says.
It’s what gets
filed, sent, approved, or executed under your name.
Most firms now govern:
- data (privacy, lineage, retention),
- models (testing, monitoring, guardrails), and
- security (identity, network, secrets).
All necessary. All downstream.
What’s been missing is the layer that decides whether a high-risk action is allowed to run at all.
That missing discipline is
Action Governance.
The architecture category that solves it is
Refusal Infrastructure for Legal AI.
What Refusal Infrastructure for Legal AI Is
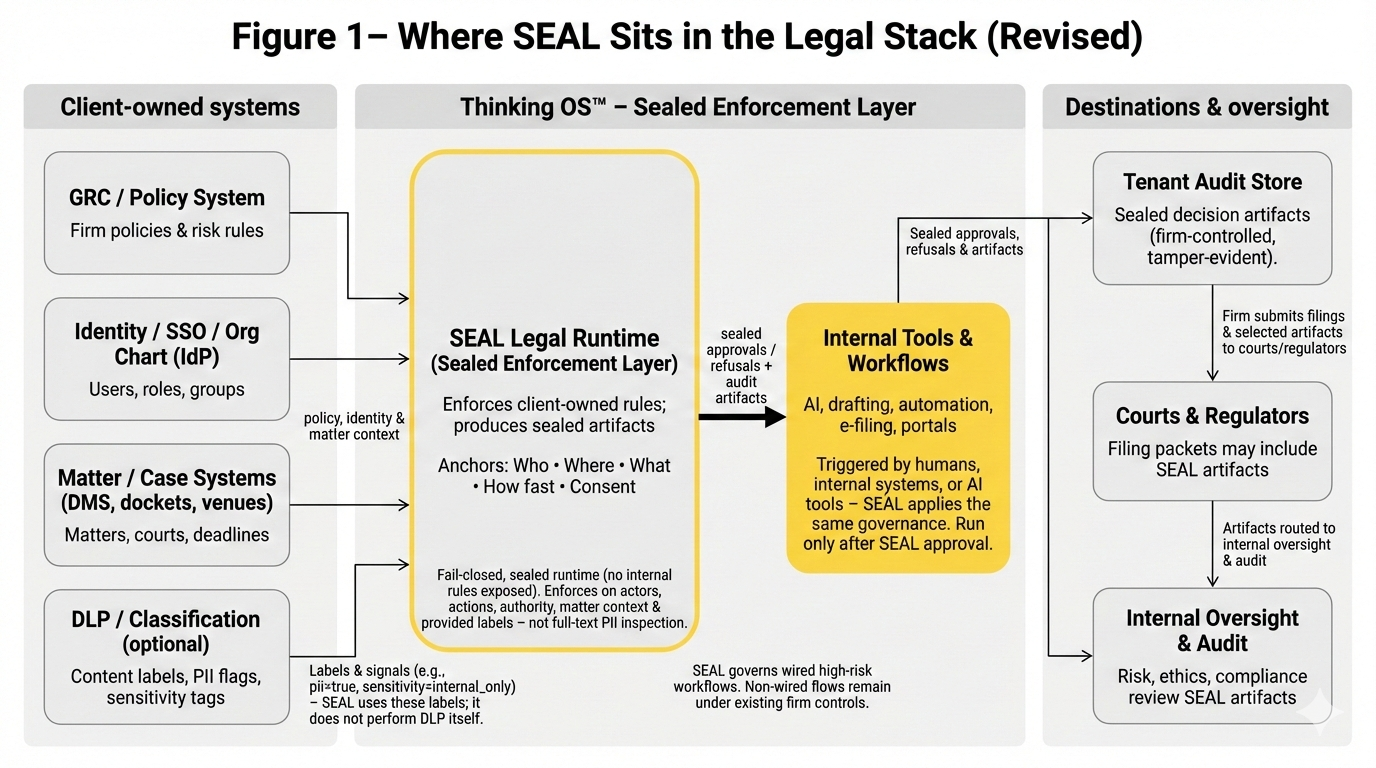
Refusal Infrastructure for Legal AI is a sealed governance layer in front of high-risk legal actions.
It sits between your internal tools and the outside world and applies Action Governance before anything can be filed, sent, or executed.
At runtime, it decides for each attempted action:
May this action proceed, must it be refused, or does it require supervision?
Instead of hoping training, policies, or dashboards will prevent bad outcomes later, Refusal Infrastructure enforces a pre-execution authority gate:
- Approve – the action may proceed under your rules.
- Refuse – the action is blocked and does not execute.
- Supervised override – the action is routed to a supervisor under your governance model.
This happens in wired workflows only—where the gate is structurally in the path of the action.
Action Governance: The First Principle
Every legal workflow ultimately reduces to three governed variables:
- Who may act
- On what
- Under whose authority
Action Governance is the discipline of enforcing these variables at runtime, before a filing, communication, or other high-risk action leaves the firm.
Refusal Infrastructure for Legal AI turns that principle into a live checkpoint:
“Is this specific person or system allowed to take this specific action, in this context, under this authority, right now—yes or no?”
No judgment content. No drafting. No advice.
Just a structural answer to the authority question, before anything moves.
Where the Pre-Execution Authority Gate Sits
Refusal Infrastructure is not a plugin on your model. It is a governance layer at the execution boundary:
- Upstream of output – before AI-assisted or human-initiated actions are filed or sent.
- Downstream of identity and policy – after roles, verticals, and matter policies are defined in your own systems.
- Inside wired workflows – non-bypassable within the legal workflows that are routed through it.
If an action does not pass through the gate, it is outside the governed surface.
If it does pass through the gate, it is subject to
the same structural checks every time.
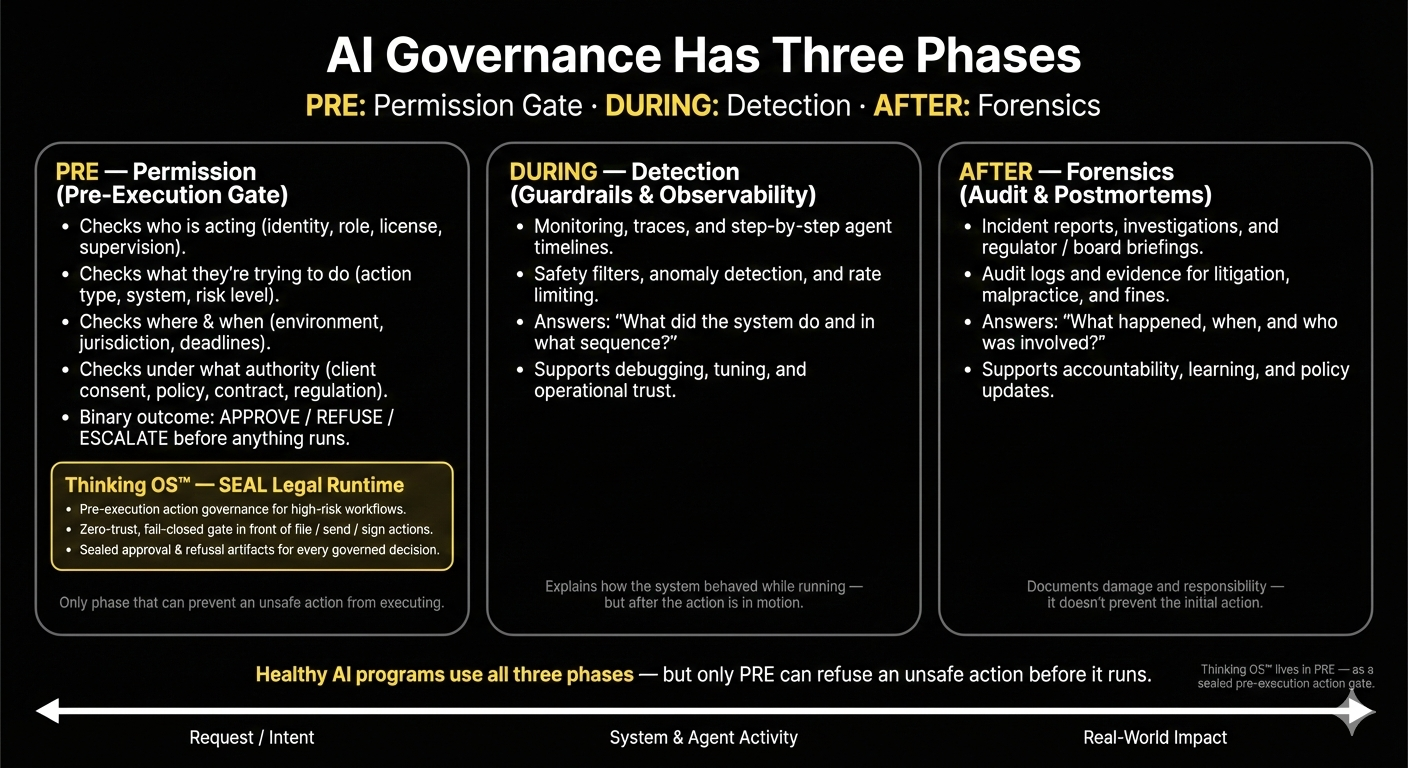
Wired Workflows and the Governance Boundary
Refusal Infrastructure is non-bypassable within wired workflows.
That means:
- For any workflow wired to the execution gate, there is no alternate “approve” path that skips Action Governance.
- Coverage is expanded by wiring more high-risk actions through the gate—not by claiming universal control over every system in the environment.
This boundary is what makes the promise credible:
- Clear in-scope actions (governed, non-bypassable once wired)
- Clear out-of-scope actions (not yet wired, visible through your broader governance program)
Sealed Artifacts: Evidence for Every Governed Decision
Unlike logging or monitoring, Refusal Infrastructure doesn’t just observe; it leaves behind evidence.
For every governed decision—approved, refused, or supervised override—it creates a sealed decision artifact:
- a tamper-evident record of who acted, on what, under which authority, and what was decided;
- designed to be written to client-owned, append-only audit storage;
- structured for regulators, insurers, and internal oversight.
This is the difference between being able to describe your governance and being able to prove which actions were allowed to proceed under your seal.
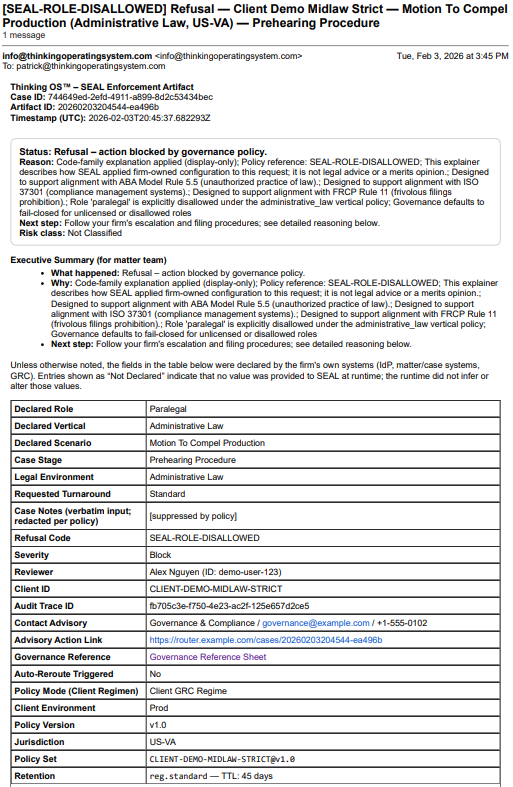
Sealed Artifact, Not a Screenshot
This is a real refusal artifact generated by Thinking OS™ when an paralegal tried to file a motion in a venue where only licensed counsel may file. The 𝗽𝗿𝗲-𝗲𝘅𝗲𝗰𝘂𝘁𝗶𝗼𝗻 𝗮𝘂𝘁𝗵𝗼𝗿𝗶𝘁𝘆 𝗴𝗮𝘁𝗲 refused the action and produced this sealed record: who acted, on what matter, under which policy/authority, and why the action was blocked.
The SEAL Legal runtime blocked the action and sealed this decision record:
who acted, what they attempted, which rules fired, and why the filing was refused—all anchored by a tamper-evident hash.
It’s evidence-grade governance documentation for insurers, regulators, and GCs, without exposing any client matter content or model prompts.
How It Differs from Other Categories
Refusal Infrastructure for Legal AI is not:
- Identity and Access Management (IAM) – IAM governs access to systems (who can log in or see a resource). Refusal Infrastructure governs what actions may be executed, even by properly authenticated users or agents.
- Guardrails or model safety – Guardrails shape what a model can say. Refusal Infrastructure decides whether any resulting action is allowed to run at all.
- GRC platforms or policy portals – GRC tools manage documentation, attestations, and reporting. Refusal Infrastructure is the runtime enforcement point for those policies in live workflows.
- Monitoring or observability – Observability tells you what happened. Refusal Infrastructure determines what is allowed to happen.
It is a new layer: a pre-execution authority control for high-risk legal actions.
SEAL Legal Runtime: Refusal Infrastructure for Law
SEAL Legal Runtime is Thinking OS™’s implementation of Refusal Infrastructure for Legal AI, purpose-built for law.
In legal workflows wired to SEAL Legal Runtime:
- Every high-risk action passes through a pre-execution authority gate
- Actions that are out of scope, missing required consent, or outside approved verticals are refused, not silently passed.
- Each governed decision leaves a sealed artifact designed to withstand regulatory, insurer, and court scrutiny—without exposing client matter content or model prompts.
SEAL Legal Runtime does not draft documents, provide legal advice, or replace attorney judgment.
It provides
refusal infrastructure and evidence so legal leaders can trust what their AI-driven stack is allowed to do.
Who Refusal Infrastructure Is For
For Law Firms and In-House Legal Teams
That want structural control over what can be filed, sent, or executed under the organization’s name.
For General Counsel and Risk Leaders
Who need more than policies and logs—they need a runtime gate and sealed artifacts.
For Legal Tech Vendors
That need a standard way to plug Action Governance into their products without rebuilding their models.
Refusal Infrastructure for Legal AI is a pre-execution authority control for high-risk legal actions. It implements Action Governance by placing a sealed governance layer (SEAL Legal Runtime) in front of wired legal workflows. At runtime—before anything is filed, sent, or executed—it decides whether an action may proceed, must be refused, or requires supervision, and produces a sealed, tamper-evident artifact for every governed decision. It is not IAM, not model guardrails, and not GRC; it is a separate execution-time governance layer.
Thinking OS™ is refusal infrastrcuture for high risk actions.
- It doesn’t tell machines what to say.
- It governs what may be filed, sent, approved, or executed at all, under configured governance rules.
Not an assistant. Not a feature.
A sealed substrate — built for moments where decisions have to stand up to courts, regulators, and time.