What Thinking OS Does
Thinking OS™ is a sealed governance runtime that sits upstream of your drafting tools and filing systems, enforcing your firm’s own rules before a motion, notice, or communication goes out the door.
It does not draft, advise, or practice law.
It enforces the guardrails your lawyers have already approved.
For every governed request, it returns approve, refuse, or route for supervision, plus a sealed decision artifact.
Thinking OS™ is a governance control. It does not provide legal advice, predict case outcomes, or replace attorney judgement.
Attorneys remain fully responsible for all filings and decisions.
Evidence That
Stands Up to Scrutiny
Auditability that behaves like a transcript, not a dashboard.
Every approval or refusal creates a sealed artifact:
- Who tried to do what, in which matter.
- Under which role, vertical, and urgency.
- What Thinking OS™ did (approved, refused, escalated) and why.
Each artifact is:
- Hashed and sealed so changes are detectable.
- Timestamped and signed for chain-of-custody.
- Stored in a tamper-evident audit trail your firm controls.
That gives you:
- Evidence-ready records for discovery, investigations, or regulator inquiries.
- Fewer gray areas when ethics or risk are reconstructing “what happened and when.”
- A concrete evidence trail instead of “we think the system blocked that.”
Admissibility Without Oversharing
Refusal and approval artifacts are engineered to support evidentiary use:
- They show what was allowed or refused and the configured rationale.
- They omit prompts, model internals, and nonessential matter detail.
- They are structured so firms can redact or segment privileged content if needed.
You get:
- Confidence that you can produce governance evidence without exposing how a client thinks or how your lawyers reason.
- Proof of enforcement your regulators, auditors, and insurers can actually read.
(Actual admissibility always depends on the rules of evidence and the court; Thinking OS™’s job is to make the artifacts worth offering.)
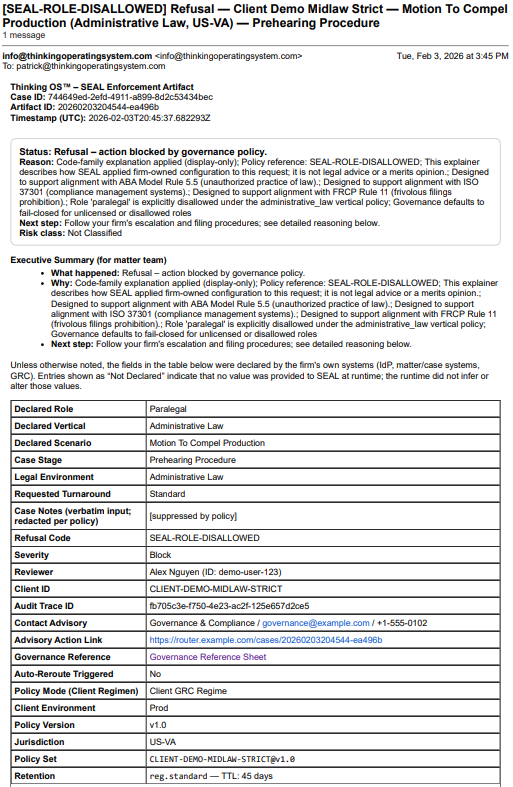
Sealed Artifact, Not a Screenshot
This is a real refusal artifact generated by Thinking OS™ when an paralegal tried to file a motion in a venue where only licensed counsel may file. The 𝗽𝗿𝗲-𝗲𝘅𝗲𝗰𝘂𝘁𝗶𝗼𝗻 𝗮𝘂𝘁𝗵𝗼𝗿𝗶𝘁𝘆 𝗴𝗮𝘁𝗲 refused the action and produced this sealed record: who acted, on what matter, under which policy/authority, and why the action was blocked.
The SEAL Legal runtime blocked the action and sealed this decision record:
who acted, what they attempted, which rules fired, and why the filing was refused—all anchored by a tamper-evident hash.
It’s
evidence-grade governance documentation for insurers, regulators, and GCs without exposing any client matter content or model prompts.
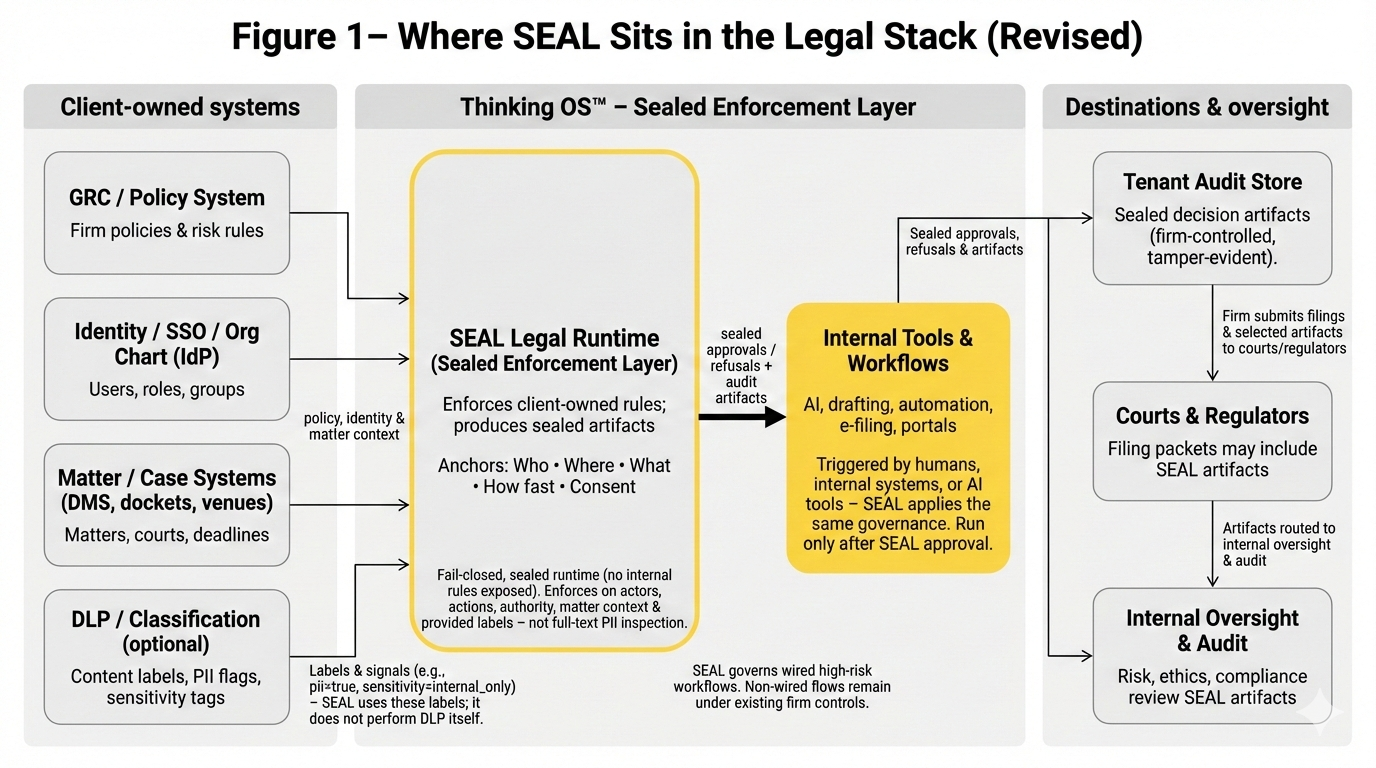
Our runtime sits between legal workflows and the outside world and answers a single question:
“W𝗵𝗼 𝗺𝗮𝘆 𝗮𝗰𝘁, 𝗼𝗻 𝘄𝗵𝗮𝘁, 𝘂𝗻𝗱𝗲𝗿 𝘄𝗵𝗮𝘁 𝗮𝘂𝘁𝗵𝗼𝗿𝗶𝘁𝘆,
𝗶𝗻 𝘁𝗵𝗶𝘀 𝗰𝗼𝗻𝘁𝗲𝘅𝘁, 𝗮𝘁 𝘁𝗵𝗶𝘀 𝗺𝗼𝗺𝗲𝗻𝘁 ?”
Refusal as Protection, Not Punishment
Thinking OS™ is built on a simple idea:
better a sealed “no” now than a sanctions order later.
When Thinking OS™ refuses, it doesn’t just say “blocked”:
- Every refusal carries a code and a short, human-readable rationale.
- Each code is mappable to your firm’s frameworks (ethics rules, ISO 37301, FRCP, internal policies).
- The artifact tells you who should fix what (role, consent, vertical, motion, evidence, authority, flood, etc.).
For your teams, refusals become structured alerts:
- “This motion is outside the allowed vertical.”
- “Consent is missing for this client.”
- “Role not authorized for this filing.”
Not: “This filing is illegal.”
Instead: “This doesn’t meet the conditions your firm configured.”
Approvals: Preconditions, Not Permission Slips
SEAL also issues approvals – but they are necessary, not sufficient, to act.
- An approval means: “This request satisfies the firm’s configured governance criteria.”
- It does not mean: “This is strategically wise, legally correct, or ethically safe.”
Lawyers still:
- Exercise professional judgment.
- Own strategy and client counseling.
- Supervise any work product that follows.
- SEAL keeps your internal rules applied consistently; it does not replace the lawyer standing behind the filing.
Who Owns the Rules (and the Practice of Law)
To keep bars comfortable and roles clean:
- Vertical policies and motion rules are authored and owned by the firm’s legal leadership or their designated advisors.
- Thinking OS™ does not decide which filings are lawful or advisable in any jurisdiction.
- We provide the sealed enforcement layer; you provide the standard of care.
Thinking OS™ stays on the governance / infrastructure side of the line, not in the practice of law.
Confidentiality, Data Handling, and Vendors
SEAL is designed for firms that can’t afford a casual data story.
- Artifacts and logs are transmitted over encrypted channels and stored in tenant-scoped audit stores.
- Thinking OS personnel access artifacts only for support or incident response, under role-based access controls and logging.
- When external services are used (e.g., for normalization or classification), they are configured under “no training on customer data”–style commitments and treated as subprocessors in DPAs.
- Your firm decides how long to retain artifacts and how to incorporate them into your own matter systems.
In short: sealed governance, not a data-mining layer.
Stopping Drift Before It Starts
Most “AI governance” waits until after a model has already hallucinated, leaked, or drifted.
SEAL enforces refusal upstream:
- Before orchestration or model calls.
- Before an unlicensed role can fire a high-risk motion.
- Before a non-consented client ID can be used for a filing.
This reduces:
- The risk of mis-authorized or mis-filed submissions.
- The likelihood of regulatory findings or fines tied to “we had no effective controls.”
- The number of human hours spent cleaning up after tools.
The Bottom Line for Law Firms
For law firms, refusal is protection:
- Protection against AI drift and unlicensed actions.
- Protection against surprise in regulatory reviews.
- Protection against “we can’t reconstruct what happened.”
- Protection for the attorneys whose names are on the filings.
Thinking OS™ doesn’t try to explain failures after the fact.
It gives you
sealed proof that you governed the decision before it ever counted against you.
How We Work With Firms Today
SEAL is being rolled out through tightly scoped enforcement pilots, not a big-bang deployment.
- We run 60–90 day enforcement windows in 1–3 wired workflows (for example: e-filing, high-risk client communications, or approvals).
- During a pilot, SEAL can only approve, refuse, or route for supervision; it never drafts or files anything on its own.
- Artifacts are tenant-scoped and firm-controlled and are designed to plug into your existing matter, risk, and audit systems.
- For 2026 we’re adding a small number of design-partner firms who want refusal infrastructure as a structural control, not just another tool.
