Your customers are wiring AI into core legal workflows.
They still expect you to answer:
“Who approved this, under what authority, and why didn’t your system stop the bad cases?”
Thinking OS™ gives your platform a sealed pre-execution authority gate in front of high-risk actions — without turning us into part of your product or rewriting your stack.
In 2026 we’re opening this up to 1–2 legal-tech design partners who want governance to be a product advantage, not an afterthought.
In One Sentence
SEAL Legal Runtime is a sealed enforcement API your product calls before high-risk actions; you keep the UI, workflows, customer, and SEAL returns an approve / refuse / supervise decision with a sealed artifact attached.
Who This Is For
You’re building software used by law firms or in-house teams, such as:
- Case / matter / practice management
- Drafting, review, research, or discovery tools (with or without AI)
- Intake, e-billing, or approvals workflows
- Risk / compliance platforms used around legal
Your product can initiate, accelerate, or automate legal actions — and your customers care deeply about governance.
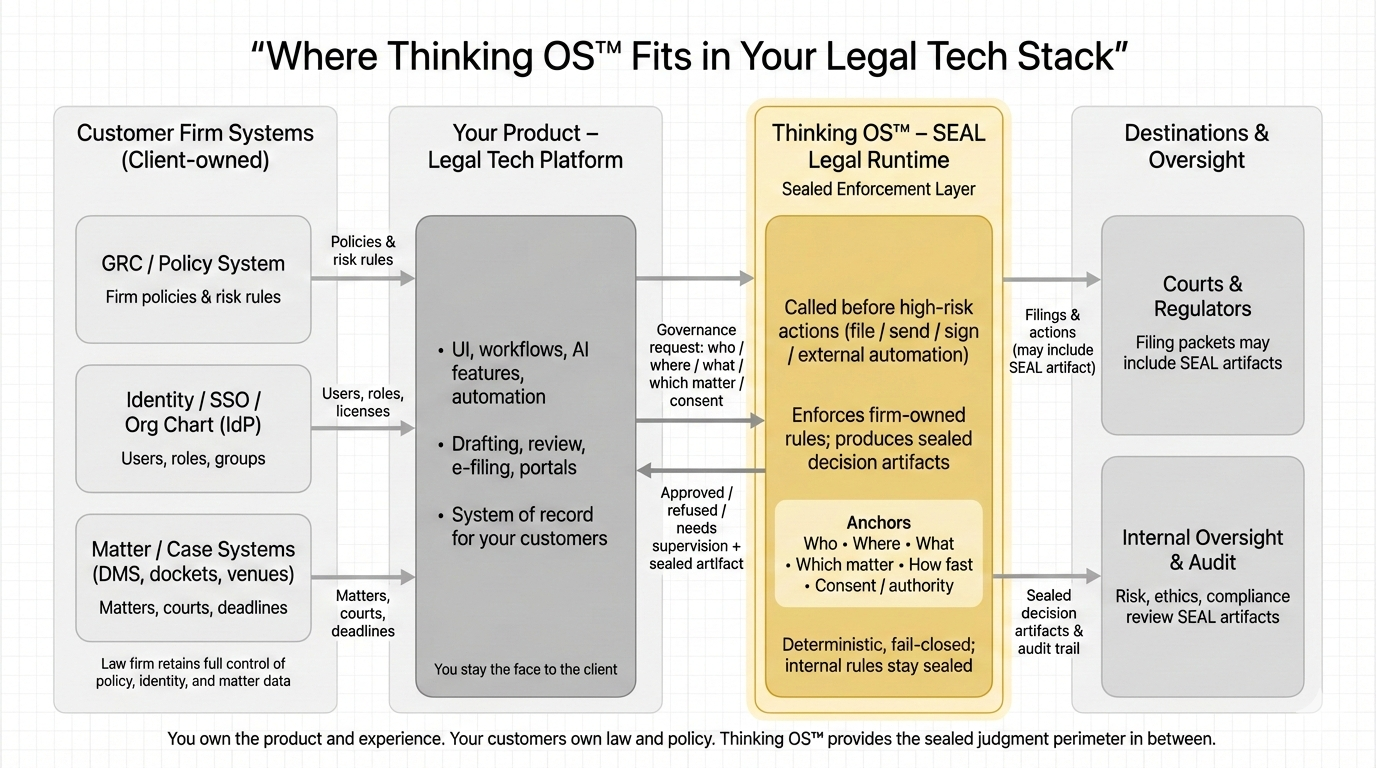
Where SEAL Sits in Your Stack
Think of SEAL as a governance nerve ending at the point where your product touches the outside world.
- Upstream: your app + IdP
- You own login, roles, groups, matter context, deadlines.
- SEAL Legal Runtime (Thinking OS™):
- Receives a small “intent” payload: who is acting, on what, in which matter, how urgent, under what authority.
- Decides: ✅ approve / ⛔ refuse / ⚠️ needs supervision.
- Emits a sealed decision artifact with IDs + hashes.
- Downstream: your normal flows
- On approval: you keep doing what you already do today, just with a SEAL decision ID on the event.
- On refusal: you halt the action and show your user SEAL’s refusal outcome.
You
stay the system of record and user experience.
We are the sealed judgment perimeter between your product and the court, regulator, or counterparty.
What Changes — and What Doesn’t
Once SEAL is wired in, three things change for your platform:
- You add a single enforcement call before high-risk actions (generate + send, file, export, approve).
- You log SEAL decision IDs and hashes alongside your own events.
- You stop baking governance rules into code; you pass identity + context into SEAL and treat its answer as the source of truth for that action.
Everything else stays yours:
- Your models, prompts, and AI agents
- Your UX, workflows, and system of record
- Your customer contracts and commercial terms
SEAL never asks for DMS / database access, doesn’t see full documents, and doesn’t train on your prompts or your customers’ matter data.
Risk & Responsibility: Clear Split
Vendors often worry about “outsourcing part of our source code.” The model here is the opposite: you keep the product; we own the authority gate.
From the vendor overview:
- Your customers own law and policy. They decide what their approval rules are.
- SEAL enforces those rules at runtime and produces sealed artifacts.
- You own how your product calls SEAL and respects the outcome.
Concrete implications:
- If SEAL refuses and your app blocks the action, your logs show:
“User X attempted Y at time T; SEAL decision_id = D; outcome = refused.” - If something goes wrong, incident response is cleaner, not heavier: your logs + our artifact join via IDs and hashes; nobody is diffing screenshots.
Professional responsibility always remains with the firm’s lawyers. SEAL is not a shadow practice group or “AI lawyer.”
Data & IP Boundary
Your customers stay in charge of law and policy. You stay in charge of your product.
- Firms author the rules; SEAL enforces those written policies and license scopes — it does not decide what is legally advisable.
- Thinking OS™ never asks for DMS or database access; SEAL works at the edge and only sees the minimum structured context needed to govern a request.
- No model tuning, no prompt access, no using decision artifacts to train public models or other customers’ systems.
You get a sealed judgment perimeter; your internals stay yours.
Integration at a Glance
What your engineers actually build:
- Identify 2–3 governed actions in your product (e.g., “send AI-drafted letter externally,” “file motion,” “export privileged set”).
- Before those actions execute, your service:
- Collects the identity + matter + action context you already know.
- Calls SEAL’s enforcement API with that payload.
- Branches on the result (approve / refuse / supervise) and logs decision_id + hashes.
No new UI is required; you decide how much of SEAL’s explanation you surface.
Under the hood we support multiple integration patterns (light pilot and stricter gating mode), but your public story is simple: “We call an external governance gate before high-risk actions; the firm owns policy; SEAL enforces; we obey.”
Built to Scale With Your Customers
Governance shouldn’t be a one-off feature for your biggest client.
- One SEAL runtime can serve multiple tenants via API, each with its own roles, motions, and consent rules.
- The runtime is built for elastic cloud scale, so governed decisions grow with usage, not headcount.
- Your team avoids a sprawl of custom moderation rules; you integrate once, then route high-risk actions through the gate.
You don’t bolt on governance per deal — you inherit an enforcement layer that grows with your customer base.
Why Become a Design Partner
We’re deliberately looking for 1–2 best-in-class platforms to harden and scale this pattern with.
As a design partner you get:
- Category advantage
- You can answer RFP and GC questions with: “Yes, we have a sealed pre-execution authority gate with evidence-grade artifacts.”
- Governance as a feature, not a PDF
- You can show customers concrete enforcement, not just policies and SOC reports.
- Differentiation in high-trust deals
- For risk-sensitive firms, “we’re wired to Thinking OS™” becomes part of your moat.
- Co-design, not a black box
- We work with your product, security, and architecture leads to pick the right integration pattern and keep the surface narrow and stable.
You’re not betting your roadmap on us; you’re adding a governance layer your biggest customers already wish existed.
What the Design-Partner Program Looks Like
We keep it small on purpose.
2026 Design-Partner Window
- Scope: 1–3 governed workflows (per partner) where a SEAL gate would remove real malpractice / regulatory risk.
- Pattern: Start with a light pilot integration (minimal payload, simple wiring), then move to a stricter gating mode once we’re both happy.
- Support:
- Dedicated integration channel with our architecture + systems-integration leads
- Access to vendor integration overview + integration brief (under NDA)
- Joint language you can reuse in RFPs and client conversations.
- Commercials:
- Intro pricing aligned with your existing tiers
- Clear separation between your SaaS agreement and your customers’ SEAL licenses
How to Tell If This Is Worth Your Time
This is probably for you if:
- Your customers are already asking about AI risk, bar rules, or governance.
- You’re tired of solving “who may do what, under what authority” in app logic for every enterprise deal.
- You’d like your answer to “what stopped this from going out?” to be something stronger than “we have logs.”
It’s probably not for you (yet) if you:
- Only handle low-risk, internal-only tasks
- Don’t touch filings, external sends, approvals, or high-stakes exports
- Don’t have customers asking for governance or auditability
Proof Over Promises
Clients and regulators don’t want assurances, they want evidence.
SEAL artifacts are:
- Tamper-evident approval, refusal, and override records (hashed, sealed, timestamped).
- Designed to be attached to matters, produced in discovery, and queried by risk & compliance teams.
- Structured so firms can map them into ABA, ISO 37301, and FRCP-style record-keeping expectations.
Trust becomes part of your infrastructure, not just a line in your sales deck.
Bottom Line for Vendors
You stay the system of record and the face to the client; Thinking OS™ is the sealed governance engine behind the scenes. Refusal becomes a product differentiator, not just a policy slide.
Next Step: Talk About a Pilot
If you’re building legal tech and this resonates, we’re looking for 1–2 design partners right now.
- The product you’re building
- The highest-risk action it can take today
- One workflow where a “nothing moves until the gate approves” guarantee would close a deal or calm a GC
We’ll share (under NDA) the private
SEAL Vendor Integration Overview and walk your team through what wiring a pre-execution authority gate into your platform really looks like.
