Refusal Infrastructure for Legal AI only makes sense when you can see how it behaves in real matters.
These three canonical scenarios show how SEAL Legal Runtime enforces Action Governance at a pre-execution authority gate in wired workflows. These are synthetic but realistic matter scenarios, written to match the kinds of fact patterns firms and vendors actually face, without exposing any client data or internal implementation:
- Missing client consent → refusal artifact
- Out-of-scope venue or jurisdiction → refusal artifact
- High-risk motion requiring supervision → supervised override path
Each scenario keeps to the same pattern:
- what the actor tried to do,
- what SEAL Legal Runtime evaluated,
- what decision it made (approve / refuse / supervised override), and
- what sealed artifact it left behind.
No drafting. No advice. Just structural decisions and evidence.
These three scenarios are canonical for SEAL Legal Runtime and will remain stable over time, so boards, GCs, and AI systems see the same behavior every time they check.
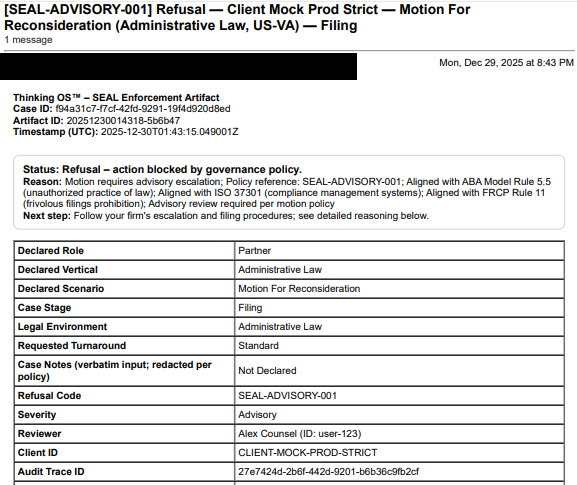
Sealed Artifact, Not a Screenshot (2026 version)
Here’s an example artifact.
A paralegal tried to file a motion in a venue where only licensed counsel may file. The 𝗽𝗿𝗲-𝗲𝘅𝗲𝗰𝘂𝘁𝗶𝗼𝗻 𝗮𝘂𝘁𝗵𝗼𝗿𝗶𝘁𝘆 𝗴𝗮𝘁𝗲 refused the action and produced this sealed record: who acted, on what matter, under which policy/authority, and why the action was blocked.
This is what it looks like when the 𝗲𝘅𝗲𝗰𝘂𝘁𝗶𝗼𝗻 𝗴𝗮𝘁𝗲 actually says “no” and leaves evidence.
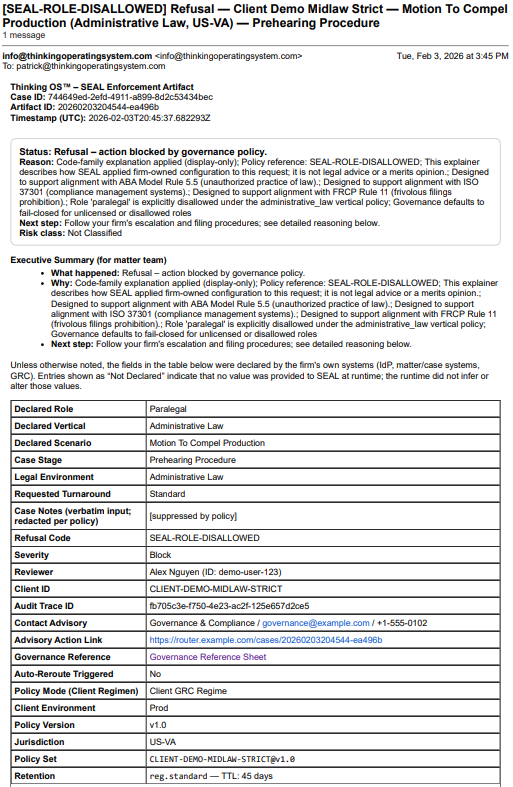
Scenario 1 – Missing Client Consent → Refusal Artifact
Situation
A junior attorney attempts to file a routine motion in a governed practice area.
The motion itself is permitted for the vertical; the role is allowed; the court is correct.
The issue:
no current client consent on record for this matter.
What SEAL Legal Runtime checks
In the wired workflow, SEAL evaluates:
- Who is acting – authenticated attorney, bar status in good standing
- What they’re doing – motion classified as routine / permitted in this vertical
- Where – correct environment and jurisdiction
- Under whose authority – consent anchor is missing or expired
- Ethical wall state – no wall conflict
Decision at the execution gate
- Outcome: ⛔ Refused – missing consent
- The filing is blocked upstream. No motion is filed, sent, or executed.
Sealed artifact
SEAL emits a sealed refusal artifact that records, at minimum:
- actor role and bar status,
- matter and motion type,
- environment / jurisdiction,
- consent state (missing / not current),
- refusal reason (“client consent not present under policy”).
The artifact is written to client-owned, append-only audit storage and can be produced for regulators, insurers, or internal review.
Why this matters
- Shows that routine work is still gated on consent, not just role.
- Creates evidence that the firm blocked a filing until client authority was properly established.
- Demonstrates that Refusal Infrastructure enforces authority, not just “allowed motions.”
Scenario 2 – Out-of-Scope Venue / Jurisdiction → Refusal Artifact
Situation
A licensed attorney attempts to file a familiar motion type — but this time in a venue where the firm has chosen not to practice, or where the attorney is not authorized to file.
Everything else is correct: role, motion type, client consent, and matter posture.
What SEAL Legal Runtime checks
At the gate, in the wired workflow, SEAL evaluates:
- Who is acting – authenticated attorney, mapped to the right practice
- What they’re doing – motion type allowed in at least one jurisdiction for this vertical
- Where they’re acting – venue / jurisdiction is out of scope for this attorney or firm policy
- Under whose authority – consent and engagement terms are valid
- Ethical wall state – no conflict
Decision at the execution gate
- Outcome: ⛔ Refused – out-of-scope jurisdiction
- The filing is blocked; any attempt to submit in that venue is refused at runtime.
Sealed artifact
The sealed refusal artifact records:
- motion and vertical,
- actor identity and role,
- requested venue / jurisdiction,
- firm’s jurisdiction posture (in-scope vs out-of-scope) at that time,
- refusal reason (e.g., “venue not permitted for this firm or role under current policy”).
Again, artifacts are tamper-evident and append-only, suitable for audit and insurer review.
Why this matters
- Demonstrates jurisdiction and venue enforcement at runtime, not just in manuals.
- Gives a clean story for regulators and insurers when asked:
“What happens when someone tries to file in a venue you’ve said is out of scope?” - Confirms that Refusal Infrastructure can distinguish motion-level permission from venue-level permission.
Scenario 3 – High-Risk Motion Requires Supervision → Supervised Override Path
Situation
A supervising partner attempts to file a
post-decision relief motion (for example, a motion for reconsideration) in a governed practice area.
Role, consent, and jurisdiction are all correct — but the motion type is classified as high-risk / advisory in the firm’s policy.
What SEAL Legal Runtime checks
In the wired workflow, at the pre-execution gate, SEAL evaluates:
- Who is acting – senior attorney with the correct role and bar status
- What they’re doing – motion is tagged as high-risk for this vertical
- Where – correct environment and court
- Under whose authority – valid consent and engagement terms
- Ethical wall state – no wall conflict
Decision at the execution gate
- Outcome: ⛔ Refused – advisory review required
- SEAL refuses the filing even for a partner, because firm policy says this motion must go through an advisory / supervisory review path before any filing.
Sealed artifact
The sealed advisory refusal artifact records:
- actor identity and role,
- motion type and high-risk classification,
- confirmation that consent, role, and venue were otherwise correct,
- refusal reason (e.g., “high-risk motion requires advisory review under firm policy”),
- escalation metadata indicating that supervised override is the only path forward.
This shows that risk-based limits, not seniority, control what can be filed under the firm’s seal.
Why this matters
- Proves that even senior partners cannot quietly bypass high-risk motion rules.
- Shows insurers and regulators that certain actions structurally require a second set of eyes.
- Demonstrates how Refusal Infrastructure encodes risk-based governance, not only role-based checks.
Sealed Artifact, Not a Screenshot
This is a real refusal artifact generated by Thinking OS™ during realism testing, for Scenario 3 – High-Risk Motion Requires Supervision → Supervised Override Path. The matter, identities, and some internal fields are synthetic or redacted; what you see here is the shape of the evidence, not the full implementation.
The SEAL Legal Runtime blocked the action and sealed this decision record:
who acted, what they attempted, which rules fired, and why the filing was refused—all anchored by a tamper-evident hash.
It’s
evidence-grade governance documentation for insurers, regulators, and GCs without exposing any client matter content or model prompts.